Is "Social Delegation" (someone the user trusts) the next factor in MFA?
Security
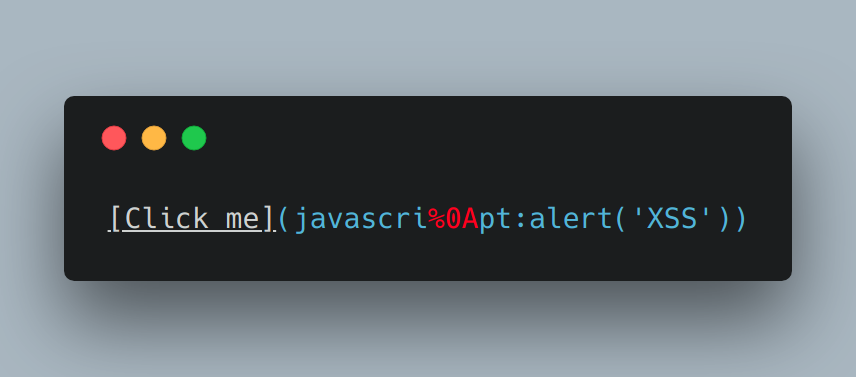
A cross-site scripting (XSS) vulnerability was found in the PHP League's CommonMark library (league/commonmark) versions 0.15.6 through 0.18.x before 0.18.1. It allows remote attackers to insert unsafe URLs into <a> tags (even if allow_unsafe_links is false) by adding an encoded newline character in the middle (e.g., writing javascript as javascri%0Apt).
Magento has just released the SUPEE-10415 security patch for the following versions:
- Magento Commerce 1.9.0.0-1.14.3.7 (formerly known as Enterprise Edition)
- Magento Open Source 1.5.0.0-1.9.3.7 (formerly known as Community Edition)
The patch contains fixed for several security vulnerabilities including cross-site request forgery (CSRF), Denial-of-Service (DoS), and authenticated Admin user remote code execution (RCE).
This project is a DIY touchscreen panel to arm/disarm Home Assistant's alarm system. It's powered by a Raspberry Pi, 3.5" touchscreen display, a custom Python-based application, and MQTT.
Check out the full build details and the source code for more.
This talk educates junior and mid-level developers on common security vulnerabilities, how they are exploited, and how to protect against them. We'll explore several of the OWASP Top 10 attack vectors like SQL injection, XSS, CSRF, and others. Each topic will be approached from the perspective of an attacker to see how these vulnerabilities are detected and exploited using several realistic examples. We'll then apply this knowledge to see how web applications can be secured against such vulnerabilities.
The goal of this talk is to educate developers on common security vulnerabilities, how they are exploited, and how to protect against them. We'll explore several of the OWASP Top 10 attack vectors like SQL injection, XSS, CSRF, session hijacking, and insecure direct object references. Each topic will be approached from the perspective of an attacker to see how these vulnerabilities are detected and exploited using several realistic examples.
This talk educates developers on common security vulnerabilities, how they are exploited, and how to protect against them. We'll explore several of the OWASP Top 10 attack vectors like SQL injection, XSS, CSRF, and others. Each topic will be approached from the perspective of an attacker to see how these vulnerabilities are detected and exploited using several realistic examples. We'll then apply this knowledge to see how web applications can be secured against such vulnerabilities.
The goal of this talk is to educate developers on common security vulnerabilities, how they are exploited, and how to protect against them. We'll explore several of the OWASP Top 10 attack vectors like SQL injection, XSS, CSRF, session hijacking, and insecure direct object references. Each topic will be approached from the perspective of an attacker to see how these vulnerabilities are detected and exploited using several realistic examples.
The goal of this talk is to educate developers on common security vulnerabilities, how they are exploited, and how to protect against them. We'll explore several of the OWASP Top 10 attack vectors like SQL injection, XSS, CSRF, session hijacking, and insecure direct object references. Each topic will be approached from the perspective of an attacker to see how these vulnerabilities are detected and exploited using several realistic examples.
This talk educates developers on common security vulnerabilities, how they are exploited, and how to protect against them. We will explore several of the OWASP top 10 attack vectors, such as SQL injection, XSS, CSRF, and session hijacking. Each topic will be approached from the perspective of an attacker to learn how these vulnerabilities are detected and exploited using several realistic examples. We will then apply this knowledge to learn how web applications can be secured against such vulnerabilities.